Professional Documents
Culture Documents
An Efficient and Scalable Framework For Peer-to-Peer Clustering and Firework Query Model
Uploaded by
Editor IJAERDOriginal Title
Copyright
Available Formats
Share this document
Did you find this document useful?
Is this content inappropriate?
Report this DocumentCopyright:
Available Formats
An Efficient and Scalable Framework For Peer-to-Peer Clustering and Firework Query Model
Uploaded by
Editor IJAERDCopyright:
Available Formats
e-ISSN (O): 2348-4470
Scientific Journal of Impact Factor (SJIF): 4.72
p-ISSN (P): 2348-6406
International Journal of Advance Engineering and Research
Development
Emerging Technologies in the Computer World, January -2017
An Efficient and Scalable Framework for Peer-to-Peer Clustering and Firework
Query Model
Prof. Shilpa Pimpalkar, Department of Computer Engineering, AISSMSs IOIT
Bhosale Prachi1, Gadve Vaishnavi2, Khopade Mayuri3, Pawar Kajal4.
Computer Engineering, AISSMSs IOIT
Abstract Efficient and trustworthy file querying is very important to the general performance of peer-to-peer (P2P)
file sharing systems. rising strategies area unit setting out to address this challenge by exploiting on-line social networks
(OSNs). However, current OSN-based strategies merely cluster common-interest nodes for prime potency or limit the
interaction between social friends for prime trustiness, that provides restricted sweetening or contradicts the open and
free service goal of P2P systems. very little analysis has been undertaken to totally and hand in glove leverage OSNs
with integrated thought of proximity and interest. during this work, we tend to analyze a Bit Torrent file sharing trace,
that proves the requirement of proximity- and interest-aware bunch. supported the trace study and OSN properties, we
tend to propose a social Network integrated P2P file sharing system with increased potency and trustiness (SoNet) to
totally and hand in glove leverage the common-interest, proximity-close and trust properties of OSN friends. SoNet uses
a ranked distributed hash table (DHT) to cluster common-interest nodes, then any cluster proximity-close nodes into
subcluster, and connects the nodes in an exceedingly subcluster with social links. Thus, once queries move trustable
social links, they additionally gain higher likelihood of being with success resolved by proximityclose nodes, at the same
time enhancing potency and trustiness. The results of trace-driven experiments on the realworld Planet Lab test bed
demonstrate the upper potency and trustiness of SoNet compared with alternative systems..
Keywords-P2P,clustering,proximity,awareness
I. INTRODUCTION
Over the past few years, the Brobdingnagian quality of the web has made a major stimulation to P2P file sharing systems.
There square measure 2 categories of P2P systems: unstructured and structured. Unstructured P2P networks like Gnutella
and Freenet doesn't assign responsibility for information to specific nodes. Nodes be a part of and leave the network in
step with some loose rules. Currently, unstructured P2P networks file question technique is predicated on either flooding
wherever the question is propagated to all or any the nodes neighbors, or random-walkers wherever the question is
forwarded to haphazardly chosen neighbors till the file is found. However, flooding and random walkers cannot
guarantee information location. Structured P2P networks i.e., Distributed Hash Tables (DHTs), will overcome the
drawbacks with their options of upper potency, quantifiability, and settled information location. It strictly controlled
topologies, and their operation algorithms and information placement square measure exactly outlined supported a DHT
organisation and consistent hashing operate. The node is answerable for a key will invariably be found eventhough if the
system is in a very continuous state of modification. Most of the DHTs need O (log n) hops per operation request with (O
log n) neighbors per node, wherever n is that the variety of nodes within the system.
II.PROPOSED SYSTEM
In this paper represents a proximity-aware and interest-clustered P2P file sharing System (PAIS) on a structured P2P
system. It forms physically-close nodes into a cluster and additional teams physically-close and common-interest nodes
into a sub-cluster. It additionally places files with identical interests along and create them accessible through the DHT
Lookup() routing operate. a lot of significantly, it keeps all benefits of DHTs over unstructured P2Ps. wishing on DHT
search policy instead of broadcasting, the PAIS construction consumes abundant less value in mapping nodes to clusters
and mapping clusters to interest sub-clusters. PAIS uses associate intelligent file replication formula to additional
enhance file search potency. It creates replicas of files that area unit oft requested by a gaggle of physically shut nodes in
their location. Moreover, PAIS enhances the intra sub-cluster file looking through many approaches 1st, it additional
classifies the interest of a sub-cluster to variety of sub-interests, and clusters common-sub-interest nodes into a gaggle for
file sharing. Second, PAIS builds associate overlay for every cluster that connects lower capability nodes to higher
capability nodes for distributed file querying whereas avoiding node overload. Third, to cut back file looking out delay,
PAIS uses proactive file info assortment so a file requester will understand if its requested file is in its near nodes.Fourth,
to cut back the overhead of the file info assortment, PAIS uses bloom filter based mostly file info assortment and
corresponding distributed file looking out. Fifth, to boost the file sharing potency, PAIS ranks the bloom filter leads to
@IJAERD-2017, All rights Reserved 88
International Journal of Advance Engineering and Research Development (IJAERD)
E.T.C.W, January -2017, e-ISSN: 2348 - 4470, print-ISSN: 2348-6406.
order. Sixth, considering that a recently visited file tends to be visited once more, the bloom filter based mostly approach
is increased by solely checking the fresh added bloom filter info to cut back file looking out delay.
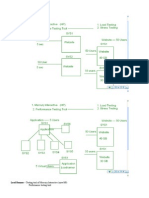
III.SYSTEM ARCHITECTURE
IV FLOWCHART
@IJAERD-2017, All rights Reserved 89
International Journal of Advance Engineering and Research Development (IJAERD)
E.T.C.W, January -2017, e-ISSN: 2348 - 4470, print-ISSN: 2348-6406.
V MATHEMATICAL MODEL
Let W be the whole system which consists:
W = {input, process, output}.
Input: {p, N, F, i}.
Where,
1. p probability of Request.
2. N is number of samples taken for estimation.
3. F is the frequency of number of events.
Process:
We implement the system that periodically transmits raw data samples at the rate of 920Hz. System
observes the transmission result of each data sample and estimates the request probability p` by
Where N is the number of observations clusters in the network, and Fi denotes the event that the i-th
transmission fails.
VI. ADVANTAGES
1. It enhances communication and availability of information.
P2P, particularly with full access to the online, permits ways in which of communication that might merely be not
possible before it had been developed. Instant electronic messaging will currently permit users to speak in real time and
send files to people where they're within the world, that could be a vast boon for businesses. Also, it permits access to a
huge quantity of helpful data, together with ancient reference materials and timely facts, like news and current events.
2. It allows for more convenient resource sharing.
This profit is extremely vital, notably for larger firms that basically have to be compelled to manufacture immense
numbers of resources to be shared to any or all the individuals. Since the technology involves computer-based work, it's
assured that the resources they needed to urge across would be utterly shared by connecting to a network that their
audience is additionally victimisation.
3. It makes file sharing easier.
P2P allows easier accessibility for people to share their files, which greatly helps them with saving more time and effort,
since they could do file sharing more accordingly and effectively.
4. It is highly flexible.
This technology is known to be very flexible, as it gives users the opportunity to explore everything about essential
@IJAERD-2017, All rights Reserved 90
International Journal of Advance Engineering and Research Development (IJAERD)
E.T.C.W, January -2017, e-ISSN: 2348 - 4470, print-ISSN: 2348-6406.
hings, such as software without affecting their functionality. Plus, people will have the accessibility to all information
they need to get and share.
5. It is an inexpensive system.
Installing networking software on your device would not cost too much, as you are assured that it lasts and can
effectively share information to your peers. Also, there is no need to change the software regularly, as mostly it is not
required to do so.
6. IT INCREASES COST EFFICIENCY.
With computer networking, you can use a lot of software products available on the market which can just be stored or
installed in your system or server, and can then be used by various workstations.
V CONCLUSION AND FUTURE SCOPE
In recent years, to boost file location potency in P2P systems, interest-clustered super-peer networks and
proximity-clustered super-peer networks are projected. though each ways improve the performance of P2P systems, few
works cluster peers supported each peer interest and physical proximity at the same time. Moreover, it's more durable to
comprehend it in structured P2P systems because of their strictly outlined topologies, though they need high potency of
file location than unstructured P2Ps. during this paper, we have a tendency to introduce a proximity-aware and interest-
clustered P2P file sharing system supported a structured P2P. It teams peers supported each interest and proximity by
taking advantage of a hierarchical data structure of a structured P2P.
We dont would like the additional proxy server to store the information backup,if one in every of node is get
unsuccessful then our system not be collapse. thus in future we are going to improve the node capability or network
affiliation.
VI APPLICATIONS
1. University and College Level
2. Business Aplication
3. Government Aplication
4. Military Aplication
VII ACKNOWLEDGMENT
We want to thank analysts and distributers for making their assets accessible. We additionally appreciative to
Commentator for their significant recommendations.
REFERENCES
[1] BitTorrent. (2013) [Online]. Available: http://www.bittorrent. com/
[2] Gnutella home page. (2003) [Online]. Available: http://www. gnutella.com
[3] I. Clarke, O. Sandberg, B. Wiley, and T. W. Hong, Freenet: A distributed anonymous information storage and
retrieval system, in Proc. Int. Workshop Des. Issues Anonymity Unobservability, 2001,pp. 4666.
[4] I. Stoica, R. Morris, D. Liben-Nowell, D. R. Karger, M. F. Kaashoek, F. Dabek, and H. Balakrishnan, Chord: A
scalable peer-topee lookup protocol for internet applications, IEEE/ACM Trans. Netw., vol. 11, no. 1, pp. 1732,
Feb. 2003.
@IJAERD-2017, All rights Reserved 91
International Journal of Advance Engineering and Research Development (IJAERD)
E.T.C.W, January -2017, e-ISSN: 2348 - 4470, print-ISSN: 2348-6406.
[5] A. Rowstron and P. Druschel, Pastry: Scalable, decentralized object location and routing for large-scale peer-to-peer
systems, in Proc. IFIP/ACM Int. Conf. Distrib. Syst. Platforms Heidelberg, 2001, pp. 329350.
[6] B. Y. Zhao, L. Huang, J. Stribling, S. C. Rhea, A. D. Joseph, and J. Kubiatowicz, Tapestry: A resilient global-scale
overlay for service deployment, IEEE J. Sel. Areas Commun., vol. 22, no. 1, pp. 4153, 2004.
[7] H. Shen, C. Xu, and G. Chen, Cycloid: A scalable constant-degree P2P overlay network, Perform. Eval., vol. 63,
pp. 195216, 2006.
[8] Z. Li, G. Xie, and Z. Li, Efficient and scalable consistency maintenance for heterogeneous peer-to-peer systems,
IEEE Trans. Parallel Distrib. Syst., vol. 19, no. 12, pp. 16951708, Dec. 2008.
[9] H. Shen and C.-Z. Xu, Hash-based proximity clustering for efficient load balancing in heterogeneous DHT
networks, J. Parallel Distrib. Comput., vol. 68, pp. 686702, 2008.
[10] FastTrack. (2003) [Online]. Available: http://www.fasttrack.nu/ index_int.html
@IJAERD-2017, All rights Reserved 92
You might also like
- Structured Peer-to-Peer Systems: Fundamentals of Hierarchical Organization, Routing, Scaling, and SecurityFrom EverandStructured Peer-to-Peer Systems: Fundamentals of Hierarchical Organization, Routing, Scaling, and SecurityNo ratings yet
- Farm Environmental Data Analyzer Using A Decentralised System and RDocument10 pagesFarm Environmental Data Analyzer Using A Decentralised System and RIJRASETPublicationsNo ratings yet
- Hierarchical Comparison and Classification of P2P Systems Based On Architectural DesignDocument10 pagesHierarchical Comparison and Classification of P2P Systems Based On Architectural DesignSaddam ShahNo ratings yet
- Zigbee Based Wireless Data AcquisitionDocument15 pagesZigbee Based Wireless Data AcquisitionanjanbsNo ratings yet
- SSW: A Small-World-Based Overlay For Peer-to-Peer SearchDocument15 pagesSSW: A Small-World-Based Overlay For Peer-to-Peer Searchsyed_zakriyaNo ratings yet
- Peer-To-Peer File SharingDocument6 pagesPeer-To-Peer File SharingVIVA-TECH IJRINo ratings yet
- A Dul WV 1597372126Document7 pagesA Dul WV 1597372126Kiya Key ManNo ratings yet
- Research Paper On Wifi PDFDocument8 pagesResearch Paper On Wifi PDFaflbmfjse100% (1)
- TMP - 11927-Information Retrieval From Big Data For Sensor Data Collection-520372139741037689682152Document3 pagesTMP - 11927-Information Retrieval From Big Data For Sensor Data Collection-520372139741037689682152Boy NataNo ratings yet
- Survey Paper On Communication System Using Blockchain and CryptographyDocument5 pagesSurvey Paper On Communication System Using Blockchain and CryptographyIJRASETPublicationsNo ratings yet
- Peer-to-Peer Networks - Protocols, Cooperation and CompetitionDocument36 pagesPeer-to-Peer Networks - Protocols, Cooperation and CompetitionTranceNo ratings yet
- Graph: RegressionDocument5 pagesGraph: RegressionDev KhandelwalNo ratings yet
- Effective and Secure Content Retrieval in Unstructured P2P Overlay Networks Using Bloom Cast TechniqueDocument6 pagesEffective and Secure Content Retrieval in Unstructured P2P Overlay Networks Using Bloom Cast TechniqueInternational Journal of computational Engineering research (IJCER)No ratings yet
- International Journal of Computational Engineering Research (IJCER)Document5 pagesInternational Journal of Computational Engineering Research (IJCER)International Journal of computational Engineering research (IJCER)No ratings yet
- Coquos Support For Continuous Queries in Unstructured P2P NetworksDocument6 pagesCoquos Support For Continuous Queries in Unstructured P2P Networkssurendiran123No ratings yet
- Multidimensional Data Management in Unstructured P2P NetworksDocument9 pagesMultidimensional Data Management in Unstructured P2P Networkseditor_ijarcsseNo ratings yet
- Big Data Analysis Using Hadoop: A Survey: August 2015Document6 pagesBig Data Analysis Using Hadoop: A Survey: August 2015DanNo ratings yet
- Secured Query Registration and Searching For P2P NetworkDocument8 pagesSecured Query Registration and Searching For P2P NetworkIJERDNo ratings yet
- SDN-accelerated HPC Infrastructure For Scientific ResearchDocument30 pagesSDN-accelerated HPC Infrastructure For Scientific ResearchSebastián E. Aliaga PereiraNo ratings yet
- Security Analysis of Handover Key Management in 4G LTE/SAE NetworksDocument4 pagesSecurity Analysis of Handover Key Management in 4G LTE/SAE NetworksadredNo ratings yet
- Peer To Peer SystemsDocument41 pagesPeer To Peer Systemsakshayhazari8281No ratings yet
- Self Chord-Achieving Load Balancing in Peer To Peer Network: M.Divya B.SaranyaDocument5 pagesSelf Chord-Achieving Load Balancing in Peer To Peer Network: M.Divya B.Saranyawww.irjes.comNo ratings yet
- A Study On Interplanetary File System Based On BlockchainDocument6 pagesA Study On Interplanetary File System Based On BlockchainVIVA-TECH IJRINo ratings yet
- Asymmetric Social Proximity Based Private Matching Protocols For Online Social Networks-IJAERDV04I0156616Document5 pagesAsymmetric Social Proximity Based Private Matching Protocols For Online Social Networks-IJAERDV04I0156616Editor IJAERDNo ratings yet
- Mobigrid: Peer-To-Peer Overlay and Mobile Ad-Hoc Network Rendezvous - A Data Management PerspectiveDocument12 pagesMobigrid: Peer-To-Peer Overlay and Mobile Ad-Hoc Network Rendezvous - A Data Management PerspectivekanjaiNo ratings yet
- Developing A Reliable Service System For Charity DonationDocument7 pagesDeveloping A Reliable Service System For Charity DonationIJRASETPublicationsNo ratings yet
- Resource Discovery Mechanisms For Peer-To-Peer SystemsDocument5 pagesResource Discovery Mechanisms For Peer-To-Peer SystemsJeannette FrazierNo ratings yet
- Looking Up Data in P2P Systems: Hari Balakrishnan, M. Frans Kaashoek, David Karger, Robert Morris, Ion StoicaDocument5 pagesLooking Up Data in P2P Systems: Hari Balakrishnan, M. Frans Kaashoek, David Karger, Robert Morris, Ion Stoicatalhakamran2006No ratings yet
- Distributed Systems Lab 2Document34 pagesDistributed Systems Lab 2Ferenc BondarNo ratings yet
- International Journal of Computer Science & Information SecurityDocument92 pagesInternational Journal of Computer Science & Information SecurityDhinaNo ratings yet
- Document Clustering: Alankrit Bhardwaj 18BIT0142 Priyanshu Gupta 18BIT0146 Aditya Raj 18BIT0412Document33 pagesDocument Clustering: Alankrit Bhardwaj 18BIT0142 Priyanshu Gupta 18BIT0146 Aditya Raj 18BIT0412Aman KushwahaNo ratings yet
- Research Paper On Network MonitoringDocument4 pagesResearch Paper On Network Monitoringzejasyvkg100% (1)
- Nuredin Ppt. RMDocument13 pagesNuredin Ppt. RMNuredin AbdumalikNo ratings yet
- Book Record Management APIDocument4 pagesBook Record Management APIIJRASETPublicationsNo ratings yet
- Itjdm 07Document91 pagesItjdm 07Paturi Pradeep GoudNo ratings yet
- Sharing Ad HocDocument9 pagesSharing Ad HocTonie NurcahyoNo ratings yet
- Project ProposalDocument20 pagesProject ProposalMajestyNo ratings yet
- Maverick - Voice Assistant Using PythonDocument6 pagesMaverick - Voice Assistant Using PythonIJRASETPublicationsNo ratings yet
- Real Datasets For File Sharing Peer To PDocument12 pagesReal Datasets For File Sharing Peer To PAdeyeye LawrenceNo ratings yet
- Content Based Retrieval in Unstructured P2P Overlay NetworksDocument6 pagesContent Based Retrieval in Unstructured P2P Overlay NetworkstheijesNo ratings yet
- Project Phase I: Guided By, Presented byDocument16 pagesProject Phase I: Guided By, Presented byJothi KumarNo ratings yet
- Smart Wi-Fi Dustbin System-IJAERDV04I0479866Document4 pagesSmart Wi-Fi Dustbin System-IJAERDV04I0479866Ajit upadhyayNo ratings yet
- Cybersecurity of Digital 2021Document267 pagesCybersecurity of Digital 2021Márk SzűcsNo ratings yet
- Achieving_Searchable_and_Privacy-Preserving_Data_Sharing_for_Cloud-Assisted_E-Healthcare_System-1Document12 pagesAchieving_Searchable_and_Privacy-Preserving_Data_Sharing_for_Cloud-Assisted_E-Healthcare_System-1votantai14102004No ratings yet
- Internet of Things Xia YangDocument3 pagesInternet of Things Xia YangPrashant PathakNo ratings yet
- Finding Experts in Community Based Question-Answering Services-IJAERDV04I0115724Document6 pagesFinding Experts in Community Based Question-Answering Services-IJAERDV04I0115724Editor IJAERDNo ratings yet
- Etrog Ethereum Based Social MediaDocument8 pagesEtrog Ethereum Based Social MediaIJRASETPublicationsNo ratings yet
- documentationDocument27 pagesdocumentationbalasubramanian2677No ratings yet
- Information Fusion-Oriented Design and Application of Multiprocessor Computer Software and HardwareDocument9 pagesInformation Fusion-Oriented Design and Application of Multiprocessor Computer Software and HardwareAldi GamingNo ratings yet
- Enhancing and Analyzing Search Performance in Unstructured Peer To Peer Networks Using Enhanced Guided Search Protocol (EGSP)Document7 pagesEnhancing and Analyzing Search Performance in Unstructured Peer To Peer Networks Using Enhanced Guided Search Protocol (EGSP)battikumarNo ratings yet
- Vol 1.2 Online Issn - 0975-4172 Print Issn - 0975-4350 September 2009Document231 pagesVol 1.2 Online Issn - 0975-4172 Print Issn - 0975-4350 September 2009Frank VijayNo ratings yet
- ResBaz 2019 Session Descriptions PDFDocument9 pagesResBaz 2019 Session Descriptions PDFMarcelo B FerreiraNo ratings yet
- Co PRIVACY PDFDocument7 pagesCo PRIVACY PDFletter2lalNo ratings yet
- DocveriferDocument8 pagesDocveriferIJRASETPublicationsNo ratings yet
- TOAST: Online ASPIC+ Implementation: Frontiers in Artificial Intelligence and Applications January 2012Document3 pagesTOAST: Online ASPIC+ Implementation: Frontiers in Artificial Intelligence and Applications January 2012patriciaNo ratings yet
- Alzahrani 2015Document8 pagesAlzahrani 2015Pedrito OrangeNo ratings yet
- Dissertation Computer NetworkingDocument4 pagesDissertation Computer NetworkingPayToWritePaperSingapore100% (1)
- Research Paper On Osi ModelDocument6 pagesResearch Paper On Osi Modelleukqyulg100% (1)
- Peer-to-Peer Grid Databases For Web Service Discovery: Wolfgang HoschekDocument48 pagesPeer-to-Peer Grid Databases For Web Service Discovery: Wolfgang HoschekIván MártonNo ratings yet
- 90 Paper WorkDocument7 pages90 Paper Workkian hongNo ratings yet
- Analysis of A Structure With Magneto-Rheological Fluid Damper-IJAERDV04I0917914Document7 pagesAnalysis of A Structure With Magneto-Rheological Fluid Damper-IJAERDV04I0917914Editor IJAERDNo ratings yet
- A Review On Solar Photovoltaic Powerplant-Ijaerdv04i0992895Document5 pagesA Review On Solar Photovoltaic Powerplant-Ijaerdv04i0992895Editor IJAERDNo ratings yet
- Antecedents of The Students' Acceptance of Online Courses - A Test of UTAUT in The Context of Sri Lankan Higher Education-IJAERDV04I0991102NDocument7 pagesAntecedents of The Students' Acceptance of Online Courses - A Test of UTAUT in The Context of Sri Lankan Higher Education-IJAERDV04I0991102NEditor IJAERDNo ratings yet
- Analysis of Vendor's For Machine Tool Manufacturing Industries With Fuzzy Inference Decision Support System - Modelling Tool-IJAERDV04I0977668Document5 pagesAnalysis of Vendor's For Machine Tool Manufacturing Industries With Fuzzy Inference Decision Support System - Modelling Tool-IJAERDV04I0977668Editor IJAERDNo ratings yet
- A Novel Design "Binary To Gray Converter" With QCA Nanotechnology-IJAERDV04I0999722Document5 pagesA Novel Design "Binary To Gray Converter" With QCA Nanotechnology-IJAERDV04I0999722Editor IJAERDNo ratings yet
- An Analysis of Water Governance in India - Problems and Remedies-IJAERDV04I0953541Document6 pagesAn Analysis of Water Governance in India - Problems and Remedies-IJAERDV04I0953541Editor IJAERDNo ratings yet
- An Improved Mobility Aware Clustering Based MAC Protocol For Safety Message Dissemination in VANET-IJAERDV04I0970094Document7 pagesAn Improved Mobility Aware Clustering Based MAC Protocol For Safety Message Dissemination in VANET-IJAERDV04I0970094Editor IJAERDNo ratings yet
- An Enhance Expert System For Diagnosis of Diabetes Using Fuzzy Rules Over PIMA Dataset-IJAERDV04I0996134Document6 pagesAn Enhance Expert System For Diagnosis of Diabetes Using Fuzzy Rules Over PIMA Dataset-IJAERDV04I0996134Editor IJAERDNo ratings yet
- Analytic Study of Phase Shift Crystal Structure and Temperature Dependent Dielectric Properties of Modified Synthesis One System Ceramics Using BNT-BZT-IJAERDV04I0937657Document6 pagesAnalytic Study of Phase Shift Crystal Structure and Temperature Dependent Dielectric Properties of Modified Synthesis One System Ceramics Using BNT-BZT-IJAERDV04I0937657Editor IJAERDNo ratings yet
- A Survey On Different Techniques of CBIR-IJAERDV04I0921177Document5 pagesA Survey On Different Techniques of CBIR-IJAERDV04I0921177Editor IJAERDNo ratings yet
- A Six-Order Method For Non-Linear Equations To Find Roots-IJAERDV04I0919497Document5 pagesA Six-Order Method For Non-Linear Equations To Find Roots-IJAERDV04I0919497Editor IJAERDNo ratings yet
- A Critical Review On Flow, Heat Transfer Characteristics and Correlations of Helically Coiled Heat Exchanger-IJAERDV04I0972560Document6 pagesA Critical Review On Flow, Heat Transfer Characteristics and Correlations of Helically Coiled Heat Exchanger-IJAERDV04I0972560Editor IJAERDNo ratings yet
- An Efficient and Secure AMDMM Routing Protocol in MANET-IJAERDV04I0874842Document9 pagesAn Efficient and Secure AMDMM Routing Protocol in MANET-IJAERDV04I0874842Editor IJAERDNo ratings yet
- A Study On Tall Structure With Soft Stories at Various Level by Non-Linear Analysis-IJAERDV04I0928305Document7 pagesA Study On Tall Structure With Soft Stories at Various Level by Non-Linear Analysis-IJAERDV04I0928305Editor IJAERDNo ratings yet
- A Study To Determine The Effectiveness of Psychoneurobics On Memory Among High School Children Aged 14 To 16 A Pilot Study-Ijaerdv04i0950904Document3 pagesA Study To Determine The Effectiveness of Psychoneurobics On Memory Among High School Children Aged 14 To 16 A Pilot Study-Ijaerdv04i0950904Editor IJAERDNo ratings yet
- A Review - On Solid Waste Management in Smart Cities-IJAERDV04I0922901Document9 pagesA Review - On Solid Waste Management in Smart Cities-IJAERDV04I0922901Editor IJAERDNo ratings yet
- Design of 5-Bit Flash ADC Through Domino Logic in 180nm, 90nm, and 45nm Technology-IJAERDV04I0819867Document6 pagesDesign of 5-Bit Flash ADC Through Domino Logic in 180nm, 90nm, and 45nm Technology-IJAERDV04I0819867Editor IJAERDNo ratings yet
- A Study On Different Failures of Composite Materials-IJAERDV04I0978320Document6 pagesA Study On Different Failures of Composite Materials-IJAERDV04I0978320Editor IJAERDNo ratings yet
- A Study On Speed Breakers-IJAERDV04I0363450Document5 pagesA Study On Speed Breakers-IJAERDV04I0363450Editor IJAERDNo ratings yet
- A Survey On Performance Evaluation of VPN-IJAERDV04I0324072Document5 pagesA Survey On Performance Evaluation of VPN-IJAERDV04I0324072Editor IJAERDNo ratings yet
- A Combined Approach WNN For ECG Feature Based Disease Classification-IJAERDV04I0932888Document8 pagesA Combined Approach WNN For ECG Feature Based Disease Classification-IJAERDV04I0932888Editor IJAERDNo ratings yet
- A Review of Studies On Ultrasonic Welding-IJAERDV04I0977419Document8 pagesA Review of Studies On Ultrasonic Welding-IJAERDV04I0977419Editor IJAERDNo ratings yet
- A Concept-Based Approach For Entity Matching-IJAERDV04I0965828Document3 pagesA Concept-Based Approach For Entity Matching-IJAERDV04I0965828Editor IJAERDNo ratings yet
- A Survey On New Horizons For Health Through Mobile Technologies-Ijaerdv04i0334966 PDFDocument6 pagesA Survey On New Horizons For Health Through Mobile Technologies-Ijaerdv04i0334966 PDFEditor IJAERDNo ratings yet
- A Survey On Content Based Video Retrieval Using Mpeg-7 Visual Descriptors-Ijaerdv04i0399438Document5 pagesA Survey On Content Based Video Retrieval Using Mpeg-7 Visual Descriptors-Ijaerdv04i0399438Editor IJAERDNo ratings yet
- A Review On Optimization of Bus Driver Scheduling-IJAERDV04I0373755Document5 pagesA Review On Optimization of Bus Driver Scheduling-IJAERDV04I0373755Editor IJAERDNo ratings yet
- A Survey On Content Based Video Retrieval Using Mpeg-7 Visual Descriptors-Ijaerdv04i0399438 PDFDocument7 pagesA Survey On Content Based Video Retrieval Using Mpeg-7 Visual Descriptors-Ijaerdv04i0399438 PDFEditor IJAERDNo ratings yet
- A Review On Mood Prediction Based Music System-IJAERDV04I0355925Document6 pagesA Review On Mood Prediction Based Music System-IJAERDV04I0355925Editor IJAERDNo ratings yet
- A Review Pneumatic Bumper For Four Wheeler Using Two Cylinder-IJAERDV04I0342284Document4 pagesA Review Pneumatic Bumper For Four Wheeler Using Two Cylinder-IJAERDV04I0342284Editor IJAERDNo ratings yet
- A Study On Improving Energy Metering System and Energy Monitoring-IJAERDV04I0346872Document4 pagesA Study On Improving Energy Metering System and Energy Monitoring-IJAERDV04I0346872Editor IJAERDNo ratings yet
- Toshiba TV ManualDocument66 pagesToshiba TV ManualLa'Mar FranklinNo ratings yet
- Lab 01Document4 pagesLab 01RapacitorNo ratings yet
- Maharishi University of Information Technology LUCKNOW (UP) - 226013Document77 pagesMaharishi University of Information Technology LUCKNOW (UP) - 226013Suraj DubeyNo ratings yet
- Work Packages and TasksDocument2 pagesWork Packages and TasksAdhiNo ratings yet
- SR OS 13.0.R10 Software Release Notes PDFDocument294 pagesSR OS 13.0.R10 Software Release Notes PDFsbalaguruNo ratings yet
- Media and Information Literacy (Mil)Document66 pagesMedia and Information Literacy (Mil)MARITES BANAYO0% (2)
- Data Warehouse Architecture and Components in 40 CharactersDocument5 pagesData Warehouse Architecture and Components in 40 CharactersVaishu SriniNo ratings yet
- The Dell Online Store Build Your SystemDocument3 pagesThe Dell Online Store Build Your SystemsathyavemuriNo ratings yet
- MGate MB3180 QIG v2Document2 pagesMGate MB3180 QIG v2RobertoFuentesNo ratings yet
- ISP Franchise Overview 10Document11 pagesISP Franchise Overview 10Bnaren Naren100% (1)
- Choosing The Ideal Indusoft Web Studio Runtime Edition Solution For Your ProjectDocument2 pagesChoosing The Ideal Indusoft Web Studio Runtime Edition Solution For Your ProjectDaniel Aguero LNo ratings yet
- ETW-REST API v1.01 Scope and SequenceDocument2 pagesETW-REST API v1.01 Scope and SequencePepito CortizonaNo ratings yet
- 7-Port Multidrop IEEE 1149.1 (JTAG) MultiplexerDocument17 pages7-Port Multidrop IEEE 1149.1 (JTAG) Multiplexergotcha75No ratings yet
- M2M MOS MapDocument644 pagesM2M MOS Mapmehran_4xNo ratings yet
- MultiMedia Quiz 6Document3 pagesMultiMedia Quiz 6Mark Anthony DagonNo ratings yet
- Proposal On Department Store Management Information SystemDocument22 pagesProposal On Department Store Management Information SystemSidra Naeem65% (20)
- Ahmed El-Tahir - Unix Linux Data Center Virtualization SME & Consultant PDFDocument2 pagesAhmed El-Tahir - Unix Linux Data Center Virtualization SME & Consultant PDFAhmed M. Ibrahim El-TahirNo ratings yet
- Step by Step Procedure To Run A Program On FPGA BoardDocument7 pagesStep by Step Procedure To Run A Program On FPGA Boardlovelyosmile253No ratings yet
- AbbreviationsDocument6 pagesAbbreviationsChidhuro OwenNo ratings yet
- Misco Home Access Welcome Guide v2Document24 pagesMisco Home Access Welcome Guide v2Marc SavageNo ratings yet
- Load Runner TrainingDocument16 pagesLoad Runner TrainingRakesh Reddy GeetlaNo ratings yet
- Ip PBX PDFDocument82 pagesIp PBX PDFTịnh TrươngNo ratings yet
- TME3413 Software Engineering Lab: Team Work & Project ManagementDocument21 pagesTME3413 Software Engineering Lab: Team Work & Project ManagementNurfauza JaliNo ratings yet
- 5Document149 pages5api-3709715No ratings yet
- RS485 PDFDocument3 pagesRS485 PDFLaurentiu Iacob100% (2)
- ABB REM Relay Unit Software Manual CAP 505Document102 pagesABB REM Relay Unit Software Manual CAP 505mitch1973100% (1)
- Cissp Security ArchitectureDocument20 pagesCissp Security Architecturefern12No ratings yet
- OTR Messages HandlingDocument14 pagesOTR Messages HandlingDineshkumar AkulaNo ratings yet
- System Center Data Protection ManagerDocument7 pagesSystem Center Data Protection ManagerjamesbNo ratings yet
- How To Install and Configure PANAgentDocument23 pagesHow To Install and Configure PANAgentd0re1No ratings yet